The Human Network is the core protocol that powers human.tech, providing keys, wallets, and identity to unlock capital flows to real humans – not bots, middlemen, or bad actors. Underneath the hood, Human Network is a decentralized threshold multi-party computation (MPC) network running as an Actively Validated Service (AVS) on Eigenlayer and Symbiotic with $1.4B in committed security.
What does the Human Network do?
The network is currently live and allows any node operator running the core libraries to join the network, compute jobs, and earn points for successful completion. The main function of the Human Network is computation of the verifiable Oblivious Pseudorandom Function (vOPRF). Nodes are incentivized to participate in rounds where encrypted shards of human data, such as what you know, what you have, or what you are, are multiplied by a point on an elliptic curve and returned to the user, where they can reconstruct a private key, a Human Key. This unlocks a variety of use-cases:
Informational-Theoretically-Secure Private Key Derivation from Human Data (biometrics, security questions, device attestations)
Verifiable Encryption Composable within ZK-SNARKs for Programmable Privacy
Secure Nullifiers for ZK Identity Proofs
How does the Human Network work?
At its core, the Human Network operates as a threshold MPC system, where a secret is securely shared among nodes. This distribution is achieved through a protocol known as Distributed Key Generation (DKG), which leverages the well-known Shamir Secret Sharing scheme. In this approach, the secret is efficiently split and distributed among the nodes in a way that ensures the overall network secret is neither fully generated nor recombined at any point. Instead, each node independently generates its private share, preserving the security and privacy of the system.
During the DKG, the threshold parameters are set up, namely n, the number of nodes sharing the secret and t, the minimum amount of private shares required to create the secret.
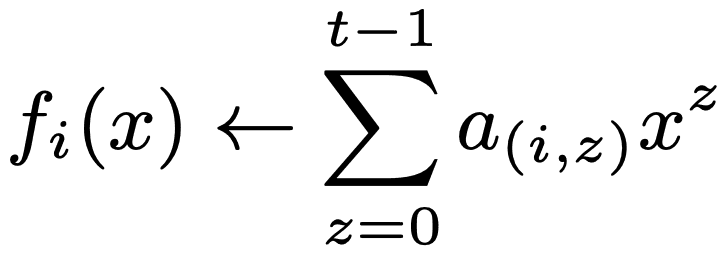
We define a time duration, called epoch, whereas a key share is valid. In other words, at the end of an epoch, all valid key shares should be renewed using a protocol named Resharing. First a new quorum of n nodes is formed and these nodes securely generate their new key shares in a similar way of the DKG protocol. We’re precise in that the quorum composition could be modified or not, and even the values of n and t could be modified during the resharing process.
As soon as the network secret is correctly distributed, the sharing nodes are then able to perform the main service of the network a distributed scalar multiplication that can be used for multiple use-cases stemming from private key derivation, verifiable encryption of a secret, or generation of a nullifier for zero-knowledge identity proofs. Network participants provide an on demand service to jointly compute the multiplication of the network secret along with a client input.
Typically this is sensitive data such as biometrics or other personal data. For example, to generate a Human Key, the nodes receive an obfuscated form of the client’s data and compute the multiplication of it with their private share. The network has guarantees that ensure participants correctly perform their functions. All nodes participating in a job are required to generate a proof that they correctly performed the multiplication using the correct values. This proof is later verified and used to ensure the network fulfills the requested service to users.
To provide security and guarantees over the nodes’ work, we combine two main approaches, namely identification and economic incentives. As identification, it means that at any step of the cryptographic protocols, if a node deviates from the protocol or sends a wrong value, it will be identified. This is made possible thanks to the way we designed our protocols.
The second approach brings security through AVS (Actively Validated Services) and restaking. It enhances economic security by allowing staked assets (ETH, LSTs, or other tokens) to be reused as collateral, increasing the cost for adversaries attempting to compromise the network. By requiring nodes to stake assets that can be slashed in case of misconduct, restaking aligns economic incentives with honest participation, deterring malicious behavior and strengthening the security and reliability of distributed networks.
For more technical information, the reader can refer to the Human Network white paper.
About Holonym Foundation
Holonym Foundation’s mission is the foundation of natural digital rights for privacy, security, and data ownership. As the parent organization of human.tech, Holonym Foundation fosters innovation through strategic partnerships, research, and advocacy, ensuring that technological advancements align with fundamental human values.
About Human Tech
Human Tech is a suite of key, wallet, and identity protocols to direct capital flow for humans - not bots, middlemen, or bad actors. human.tech is rolling out the world’s best capital allocation infrastructure to billions of humans with biometric keys, self-custodial wallets, and private identity.




